Science and Technology
In News: Apple announced it will be increasing the number of data points protected by end-to-end encryption on iCloud from 14 to 23 categories.
Context:
- With end-to-end encryption, user data will be protected even in case data is breached in the cloud. Similarly, Elon Musk wanted Twitter DMs to be encrypted.
- However, the government agencies are not happy with above developments.
- Such as , the FBI is deeply concerned with the threat of end-to-end encryption and user-only access pose as they hinder its ability to protect citizens from cyber-attacks, violence against children, and terrorism.
What is end-to-end encryption:
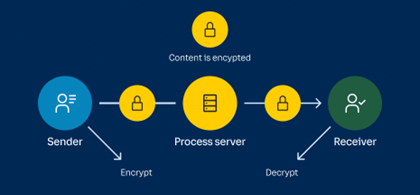
- End-to-end encryption is a communication process that encrypts data being shared between two devices.
- It prevents third parties like cloud service providers, internet service providers (ISPs) and cybercriminals from accessing data while it is being transferred.
- The process of end-to-end encryption uses an algorithm that transforms standard text into an unreadable format.
- This format can only be unscrambled and read by those with the decryption keys, which are only stored on endpoints and not with any third parties including companies providing the service.
- Apple shared that end-to-end encrypted data can only be decrypted by trusted devices where users are signed with their Apple ID. No one else can access this data and it remains secure even in the case of a data breach in the cloud storage.
Applications:
- End-to-end encryption is used to secure communications.
- Some of the popular instant-messaging apps that use it are Signal, WhatsApp, iMessage, and Google messages.
- It is also used to secure passwords, protect stored data and safeguard data on cloud storage.
- It has long been used when transferring business documents, financial details, legal proceedings, and personal conversations.
- It can also be used to control users’ authorisation when accessing stored data, which seems to be what Apple intends to do.
Significance:
- The extra layer of protection would be valuable to targets of hacking attacks launched by well-funded groups.
- It secures users’ data from snooping by government agencies, making it a sought-after feature by activists, journalists, and political opponents.
- It ensures that user data is protected from unwarranted parties including service providers, cloud storage providers, and companies that handle encrypted data.
- The data can only be accessed with access to the device passcode, password, recovery contact, or recovery key. The technology also makes it harder for service providers to share user information from their services with authorities.
Challenges of data:
- Data breach: Apple cited data breach research report, “The Rising Threat to Consumer Data in the Cloud”, stating that the total number of data breaches more than tripled between 2013 and 2021.
- Data of 1.1 billion personal records were exposed in 2021 alone.
- AIIMS servers have been hacked repeatedly.
- Non comprehensive: End-to-end encryption does not protect metadata, which includes information like when a file was created, the date when a message is sent and the endpoints between which data was shared.
- Threats of cyber-terrorism: FBI said it would enable tech companies “served with a legal order” to decrypt data
- In 2019, the U. S., the U. K., and Australia planned to pressure Facebook to create a backdoor into its encrypted messaging apps to allow governments to access the contents of private communications.
- Australia, in 2018, passed laws that would force tech companies and service providers to build capabilities allowing law enforcement secret access to messages on platforms like WhatsApp and Facebook.
Suggestions for future:
- EU’s General Data Protection Regulation (GDPR) 2018 are the most forward-thinking and extensive legal provision for the protection of personal data and its ongoing security.
- It mitigates the risks of fraud, compromise and corruption, and protects the individual.
- US’s California Consumer Privacy Act (CCPA) provides robust privacy rights and consumer protection.
- South Africa implemented Protection of Personal Information Act (POPIA) with equally stringent and rigorous personal data protection controls in place.
- Schrems II ruling addressed the flow of information from the European Union to the United States, has had an immense impact on global international privacy regulations and approaches.
- India enacted Personal Data Protection bill 2022 that embeds many of the tenets of GDPR within the country’s context.
- These include requirements for notice and prior consent for the use of individual data, limitations on the purposes for which data can be processed by companies, and restrictions to ensure that only data necessary for providing a service to the individual in question is collected.
- In 2017, a supreme court judge ruled that it was unconstitutional for private companies to use Aadhaar data – a platform that was unveiled in 2009 and forms a massive part of the country’s biometric identification programme.
Way forward:
- While cryptographers and cybersecurity experts argue that attempts by law enforcement to weaken encryption with backdoors are ill-advised and could compromise the reliability of the internet, the move by tech companies to use end-to-end encryption to secure more user data seems to be getting stronger.
- Global regulations are constantly changing and adapting to trends, international best practices, and regulatory rulings.
- However, as these changes continue, it’s likely that global requirements will align with one another more tightly to provide both country, citizen and organisation with a more solid regulatory footing.
Source: The Hindu











