Security Issues
Context: Ransomwares have emerged as the most predominant of malicious cyberattacks worldwide.
About Cyberattacks:
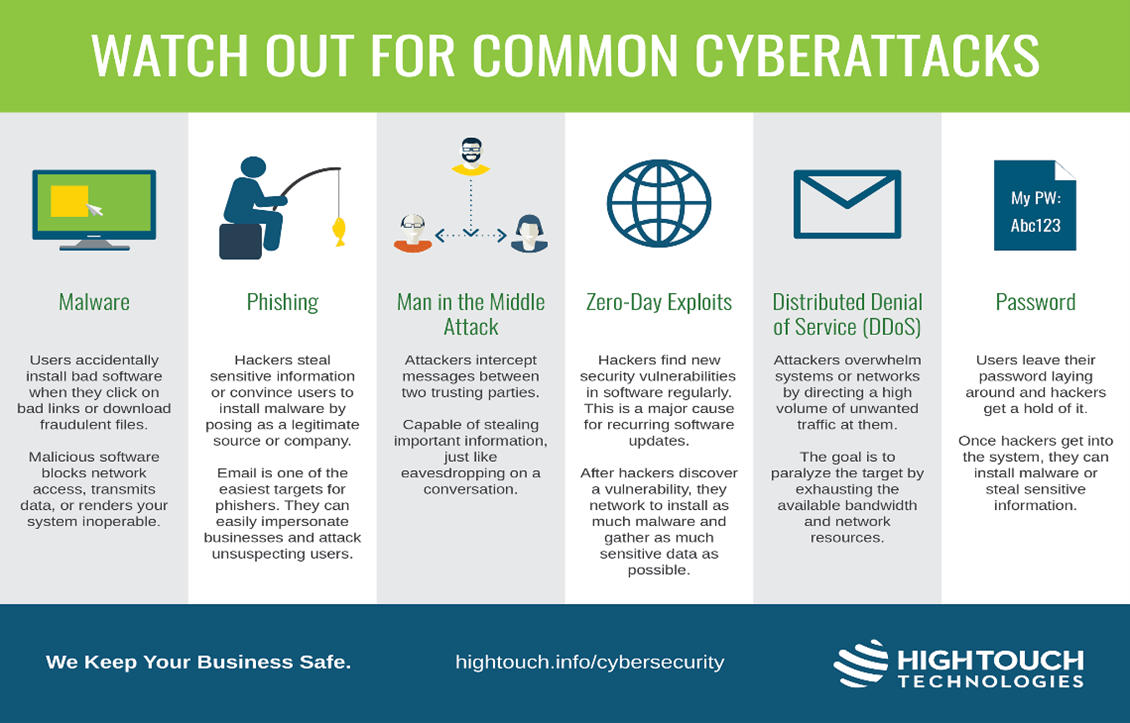
- Cyberattacks are unwelcome attempts to steal, expose, alter, disable or destroy information through unauthorized access to computer systems.
- Typically such forms of attacks to keep networks from functioning after encrypting data, are carried out by ransomware-seeking entities.
- In ransomware, the perpetrators demand hefty payments for the release of withheld data.
Recent cases of ransomware attacks
- AIIMS Cyberattack: The ransomware attack was faced by the servers of India’s premium institute, the All India Institute of Medical Sciences.
- Nearly 40 million health records were compromised and it took over two weeks for the systems to be brought online.
- Cyberattack on Solar Industries Limited: A ransomware gang, BlackCat, breached the parent company of Solar Industries Limited, one of the Ministry of Defence’s ammunition and explosives manufacturers, and extracted over 2 terabytes of data.
- Overall data: Data shows that over 75% of Indian organisations have faced such attacks, with each breach costing an average of Rs.35 crores of damage.
Reasons for increasing Cyberattacks:
- Increasing dependency on technology:
- As we grow faster, more and more systems are being shifted to virtual space to promote access and ease of use. However, the downside to this trend is the increased vulnerability of such systems to cyber-attacks.
- Asymmetric and covert warfare: Unlike, conventional warfare with loss of lives and eyeball-to-eyeball situations, cyber warfare is covert warfare with the scope of plausible deniability, i.e. the governments can deny their involvement even when they are caught.
- Therefore, cyber warfare has increasingly become the chosen space for conflict between nations.
- Lack of robust law enforcement mechanisms: India’s approach to cyber security has so far been ad hoc and unsystematic.
- Despite a number of agencies, policies and initiatives, their implementation has been far from satisfactory.
- Adverse relations with China: China is considered one of the world leaders in information technology.
- Therefore, it is expected to have capabilities to disable or partially interrupt the information technology services in another country.
- Combined with the recent border standoff and violent incidents between the armies of the two countries, the adversity in relations is expected to spill over to attacking each other’s critical information infrastructure.
- Asymmetric and covert warfare: Unlike conventional warfare with loss of lives and eyeball to eyeball situations, cyber warfare is covert warfare with the scope of plausible deniability, i.e. the governments can deny their involvement even when they are caught.
- Lack of International Coordination: International cooperation and consensus is missing in this field.
- Low digital literacy among the general public and digital gaps amongst nations create an unsustainable environment in the cyber domain.
- It is often reported that people are duped easily by click-baiting them into clicking interesting content, which often has malware attached to itself.
Challenges associated with cyberattacks:
- Need of a cyber security policy: With cyber threats capable of undermining our critical infrastructure, industry and security, a comprehensive cyber security policy is the need of the hour.
- Scarcity of workforce: Most organisations lack the tools to identify cyberattacks, let alone prevent them.
- India also faces an acute scarcity of cybersecurity professionals.
- Nearly two-thirds would find it challenging to respond to a cybersecurity incident due to the shortage of skills within their team.
- India is projected to have a total workforce of around 3,00,000 people in this sector in contrast to the 1.2 million people in the United States.
- Digital Geneva Convention: Most of our organisations are private, and their participation remains limited in India’s cybersecurity structures.
- They would be advised to look at the Digital Geneva Convention, where over 30 global companies have signed a declaration to protect users and customers from cyber breaches and collaborate with like-minded intergovernmental and state frameworks.
- Need for a global framework: With most cyberattacks originating from beyond our borders, international cooperation would be critical to keeping our digital space secure.
India’s Preparedness to Ensure Cybersecurity:
- Banning of unsafe apps: India had banned apps that posed a threat to security.
- India had banned many apps (mostly of Chinese origin), which were found to be unsafe for usage by Indian citizens.
- Awaited National cybersecurity strategy: Comprehensive plan in preparing & dealing with cyber-attacks (Pre, Post and During the attack).
- Indian Cyber Crime Coordination Centre (I4C): Launched in 2018, It is an apex coordination centre to deal with cybercrimes.
- Evolving Technology: Cyber attackers are continuously working on novel ways to sabotage the systems.
- CERT-In (Cyber Emergency Response Team, India): is an office within the Ministry of Electronics and Information Technology of the Government of India.
- It is the nodal agency to deal with cyber security threats like hacking and phishing.
- It strengthens security-related defence of the Indian Internet domain.
- National Cyber Security Policy, 2013: The policy provides the vision and strategic direction to protect the national cyberspace.
- Cyber Swachhta Kendra: Launched in 2017, these helps users to analyse and keep their systems free of various viruses, bots/ malware, Trojans, etc.
- Indian Cyber Crime Coordination Centre (I4C): Launched in 2018, It is an apex coordination centre to deal with cybercrimes.
- Cyber Surakshit Bharat: It was launched by the Ministry of Electronics and Information Technology (MeitY) in 2018 with an aim to spread awareness about cybercrime and building capacity for safety measures for Chief Information Security Officers (CISOs) and frontline IT staff across all government departments.
- The Cyber Warrior Police Force: It was organised on the lines of the Central Armed Police Force in 2018.
- Personal Data Protection Bill: The bill mandates the strengthening of data infrastructure by private companies to safeguard the data of individuals.
- Information Technology Act, 2000 (Amended in 2008): It is the main law for dealing with cybercrime and digital commerce in India.
- National Critical Information Infrastructure Protection Centre (NCIIPC) was created under Section 70A of IT Act 2000 to protect Cyberinfrastructure.
Way Forward:
- Human resource is crucial and there is an urgent need to create an informal Indian team of Cyber Warriors.
- The critical infrastructure managers should also be well trained in cyber warfare and well equipped with all the technologies for isolating viruses and attacks.
- There should be a reward for white hackers who can highlight their shortcomings.
- The managers and common mass must be made aware.
- There is a need to enhance the general awareness levels of the government installations as well as the general public to counter such threats.
- Separate wing under Army or Navy as Cyber Command on lines of US.
- The need of the hour is to come up with a futuristic National Cyber-Security Policy which allocates adequate resources and addresses the concerns of the stakeholders.
- Similarly, there is a need for quicker up-gradation of the existing infrastructure as information technology is a fast-evolving field and there is a need to stay ahead of the competition.
Cooperation with G20:
- The G-20 summit this year in India, which will see participation by all the stakeholders driving the global levers of power, is a rare opportunity to bring together domestic and international engagement groups across the spectrum, and steer the direction of these consultations.
- India could try to conceptualise a global framework of common minimum acceptance for cybersecurity.
Source: The Hindu














