Governance, Indian Polity & Constitution, Security Issues
Syllabus
- GS-2: Government policies and interventions for development in various sectors and issues arising out of their design and implementation.
- GS-3: Cyber Security
Aadhar & its Security
Context: Since the inception of the UID project, institutions and organizations have focused more on linking their databases with Aadhaar numbers and this has raised questions about the safety of the Aadhar ecosystem.
Unique Identification Development Authority of India (UIDAI) has issued an advisory asking people to refrain from sharing photocopies of their Aadhaar Card because it could be misused.
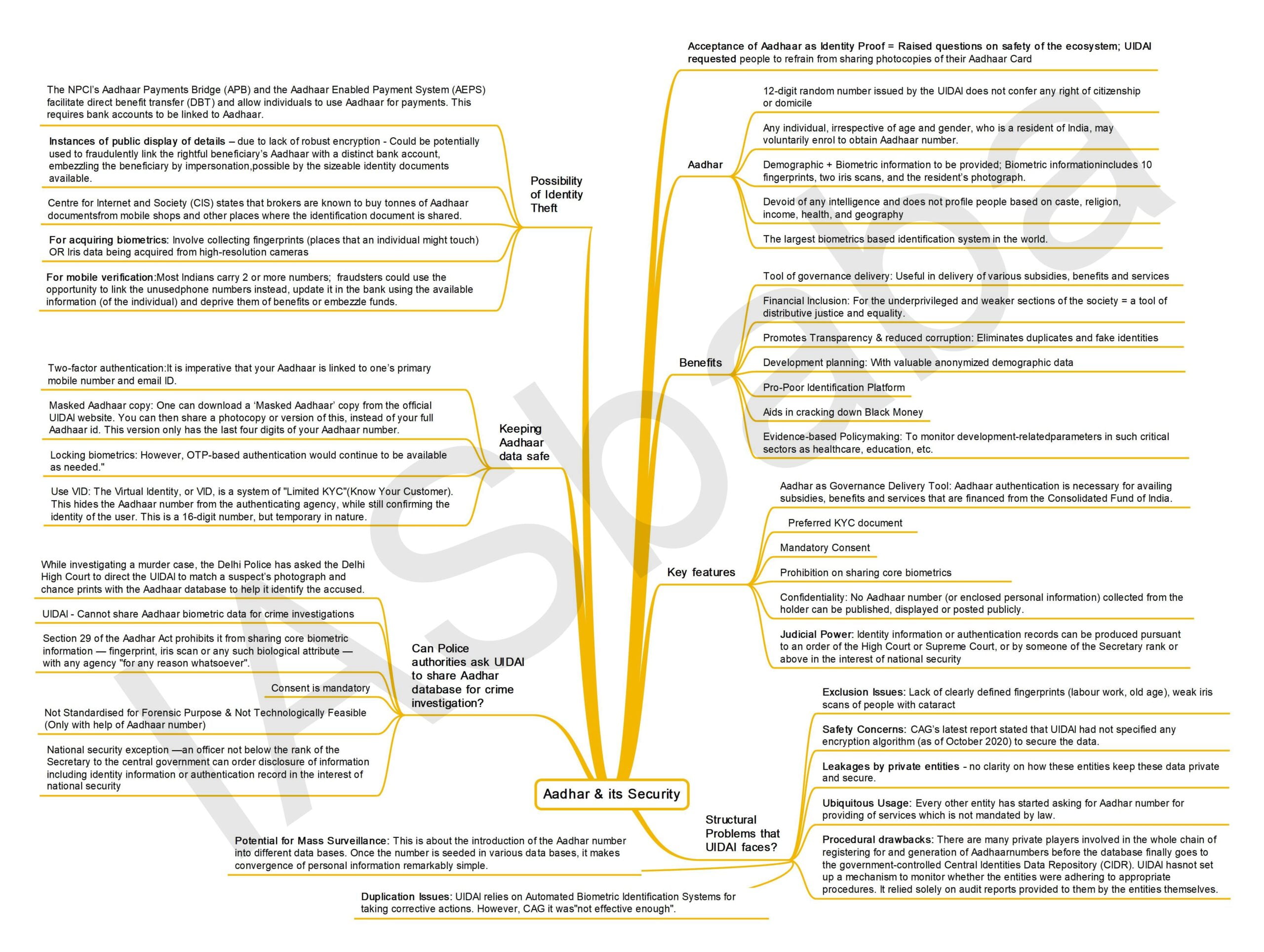
What is Aadhar?
- Aadhaar number is a 12-digit random number issued by the UIDAI (“Authority”) to the residents of India after satisfying the verification process laid down by the Authority.
- Any individual, irrespective of age and gender, who is a resident of India, may voluntarily enrol to obtain Aadhaar number.
- Person willing to enrol has to provide minimal demographic and biometric information during the enrolment process which is totally free of cost.
- Demographic information includes name, address, date of birth, gender, mobile phone number, and email address.
- Biometric information includes 10 fingerprints, two iris scans, and the resident’s photograph.
- The Aadhaar number is a proof of identity, however, it does not confer any right of citizenship or domicile in respect of an Aadhaar number holder.
- Each Aadhar number will be unique to an individual and will remain valid for life.
- Aadhar is easily verifiable in an online, cost-effective way
- Aadhaar can also be used as a permanent Financial Address.
- Aadhaar number is devoid of any intelligence and does not profile people based on caste, religion, income, health and geography
- It is by far the largest biometrics based identification system in the world.
- The UIDAI and the Aadhar project were functioning on the basis of an executive
action till 2016 since it was set up in 2011.
What are the benefits of Aadhar?
- Tool of governance delivery: Aadhaar identity platform with its inherent features of Uniqueness, Authentication, Financial Address and e-KYC, enables the Government of India to directly reach residents of the country in delivery of various subsidies, benefits and services by using the resident’s Aadhaar number only.
- Financial Inclusion: Since Aadhar also contains financial address, it facilitates financial inclusion of the underprivileged and weaker sections of the society and is therefore a tool of distributive justice and equality.
- Promotes Transparency & reduced corruption: It is unique and robust enough to eliminate duplicates and fake identities and may be used as a basis/primary identifier to roll out several Government welfare schemes and programmes for effective service delivery thereby promoting transparency and good governance.
- Development planning: Enables valuable anonymized demographic data to help
development planning at State, District and local government levels - Pro-Poor Identification Platform: People belonging to poor & marginalized sections of the society often do not have a valid proof of identity. As a result, they miss out on availing social benefits provided by the government. Aadhaar has been successful in solving this problem. One of the central properties of Aadhaar is its uniqueness and is valid for lifetime, fundamentally becoming a pro-poor identification infrastructure
- Aids in cracking down Black Money: Use of Aadhaar card in real estate transaction & bank transaction could provide trail of transactions and aid in crackdown of black money
- Evidence based Policy making: It can be used to monitor development related parameters in such critical sectors as healthcare, education, etc. It can also help to map skilled manpower, based on the vocational training acquired by the individual, to suitable job vacancies/ skill requirements of the State
What are the key features of the Aadhar Act?
- Aadhar as Governance Delivery Tool: The Aadhaar (Targeted Delivery of Financial and Other Subsidies Benefits and Services) Act, 2016 makes it clear that Aadhaar authentication is necessary for availing subsidies, benefits and services that are financed from the Consolidated Fund of India.
- In the absence of Aadhaar, the individual is to be offered an alternate means of identification to ensure she/he is not deprived of the same.
- Preferred KYC: Aadhaar has been described as a preferred KYC (Know Your Customer) document but not mandatory for opening bank accounts, acquiring a new SIM or school admissions.
- Mandatory Consent: The requesting entity would have to obtain the consent of the individual before collecting his/her identity and ensure that the information is only used for authentication purposes on the Central Identities Data Repository (CIDR)
- Prohibition on sharing core biometrics: The Aadhaar Act forbids sharing Core Biometric Information (such as finger print, iris scan, among other biometric attributes) for any purpose other than Aadhaar number generation and authentication.
- Confidentiality: The Act makes it clear that confidentiality needs to be maintained and the authenticated information cannot be used for anything other than the specified purpose. More importantly, no Aadhaar number (or enclosed personal information) collected from the holder can be published, displayed or posted publicly.
- Judicial Power: Identity information or authentication records can be produced pursuant to an order of the High Court or Supreme Court, or by someone of the Secretary rank or above in the interest of national security.
What are the structural Problems that UIDAI faces?
- Exclusion Issues: Labourers and poor people, the primary targets of the Aadhar process, often do not have clearly defined fingerprints because of excessive manual labour. Even old people with “dry hands” have faced difficulties. Weak iris scans of people with cataract have also posed problems. In several cases, agencies have refused to register them, defeating the very aim of inclusion of poor and marginalised people.
- Safety Concerns: The Aadhaar Data Vault is where all numbers collected by authentication agencies are centrally stored. Its objective is to provide a dedicated facility for the agencies to access details only on a need-to-know basis. CAG’s latest report stated that UIDAI had not specified any encryption algorithm (as of October 2020) to secure the data.
- Leakages: Many private entities in the country insist on an Aadhaar card, and users often share the details. There’s no clarity on how these entities keep these data private and secure. In the past, there have been reports of Aadhaar databases being leaked and sold.
- Ubiquitous Usage: Every other entity has started asking for Aadhar number for providing of services which is not mandated by law. More recently with Covid-19 testing, many would have noticed that most labs insist on Aadhaar card data, including a photocopy. It should be noted that it is not mandatory to share this for getting a Covid-19 test done.
- Procedural drawbacks: There are many private players involved in the whole chain of registering for and generation of Aadhaar numbers before the database finally goes to the government-controlled Central Identities Data Repository (CIDR). UIDAI has not set up a mechanism to monitor whether the entities were adhering to appropriate procedures. It relied solely on audit reports provided to them by the entities themselves.
- Duplication Issues: The CAG’s reported stated that there were issues of multiple Aadhaars to the same resident and also same biometric data being accorded to multiple residents. UIDAI relies on Automated Biometric Identification Systems for taking corrective actions. However, CAG concluded it was “not effective enough”.
- Potential for Mass Surveillance: This is about the introduction of the Aadhar number into different data bases. Once the number is seeded in various data bases, it makes convergence of personal information remarkably simple. So, if the number is in the gas agency, the bank, the ticket, the ration card, the voter ID, the medical records and so on, the state, as also others who learn to use what is called the ‘ID platform’, can ‘see’ the citizen at will.
Is identity theft via Aadhaar possible?
- The NPCI’s Aadhaar Payments Bridge (APB) and the Aadhaar Enabled Payment System (AEPS) facilitate direct benefit transfer (DBT) and allow individuals to use Aadhaar for payments. This requires bank accounts to be linked to Aadhaar.
- In 2017, researchers at the Centre for Internet and Society (CIS) acquired information of various beneficiaries of such social security and employment schemes such as their Aadhaar numbers, bank account details, job card status, mobile number etc.
- The same year, the UIDAI in response to an RTI stated that more than 200 central and State government websites publicly displayed details of some Aadhaar beneficiaries such as their names and addresses. Both were made possible by the lack of robust encryption.
- This data could be potentially used to fraudulently link the rightful beneficiary’s Aadhaar with a distinct bank account, embezzling the beneficiary by impersonation, made possible by the sizeable identity documents available.
- The UIDAI maintains that merely knowing the bank account number would not be enough to withdraw money from the bank, stating that the individual’s fingerprint, iris data or OTP to a registered mobile number would be required.
- Centre for Internet and Society (CIS) states that brokers are known to buy tonnes of Aadhaar documents from mobile shops and other places where the identification document is shared.
- Additionally, there have been instances where employees of service providers were caught stealing biometric information collected solely for Aadhaar authentication.
- A far-stretch means for acquiring biometrics would involve collecting fingerprints from varied places that an individual might touch unknowingly in a certain space (such as a railing of a staircase) with iris data being acquired from high-resolution cameras.
- As for mobile verification, phone users in India are known to carry two or more phone numbers at one time. There could be a possibility that the number linked to the Aadhaar is not prominently used. Fraudsters could use this as an opportunity to link their phone numbers instead, update it in the bank using the available information (of the individual) and deprive them of benefits or embezzle funds.
So, how does one keep one’s Aadhaar data safe?
While a regular user cannot control data breaches, there are some steps to ensure that one’s Aadhaar card number is not used by anyone else. A look at the steps to keep in mind:
- Two-factor authentication: It is imperative that your Aadhaar is linked to one’s primary mobile number and email ID. This is where UIDAI will send the one-time password (OTP) if someone tries to access your Aadhaar account or using it for any verification. If one has changed your mobile phone number for any reason, it is best to go to an Aadhaar enrolment centre and update this information as soon as possible. Aadhaar verification can only happen with this OTP.
- Masked Aadhaar copy: One can download a ‘Masked Aadhaar’ copy from the official UIDAI website. You can then share a photocopy or version of this, instead of your full Aadhaar id. This version only has the last four digits of your Aadhaar number, instead of the full number. It can be downloaded from UIDAI website itself.
- Locking biometrics: If one is worried about misuse of your Aadhaar biometric data, one can also lock it from the UIDAI website. Logging into MyAadhaar shows this as one of the options on the dashboard. According to the website, “When you lock your biometrics (fingerprint, iris, and face), they can no longer be used for authentication. However, OTP-based authentication would continue to be available as needed.”
- Users can lock this data temporarily or permanently, depending on preference, and it can be unlocked in both cases.
- Use VID: The Virtual Identity, or VID, is a system of “Limited KYC” (Know Your Customer). This hides the Aadhaar number from the authenticating agency, while still confirming the identity of the user. This is a 16-digit number, but temporary in nature. So, unlike the permanent 12-digit Aadhaar number, the VID is valid only for some time.
- The old VID expires when a new one is generated, and only one valid VID number can be there against a particular Aadhaar number at any given point in time.
- VID confirms your identity to the authenticating entity, say your bank. The VID can be generated from the Aadhaar resident portal or the mAdhaar app on iOS and Android.
What was the recent circular issued by UIDAI and why it was withdrawn?
- It had cautioned users from publicly sharing their Aadhaar numbers.
- The withdrawn notice had suggested holders use a masked Aadhaar card instead of the conventional photocopy. Masked Aadhaar’ veils the first eight digits of the twelve-digit ID with ‘XXXX’ characters.
- It also asked the public to avoid using public computers to download their e-Aadhaar.
- It stated that only those organisations that have obtained a User License from the UIDAI can use Aadhaar to establish the identity of a person.
- It added that private entities like hotels or film halls are not permitted to collect or keep copies of Aadhaar card, stating that it is an offence under the Aadhaar Act 2016.
- It asked users to verify that any private entity demanding to see the Aadhaar card should have a valid User License from the UIDAI.
- However, it withdrew the notification on the concerns that it would be misinterpreted.
Can Police authorities ask UIDAI to share Aadhar database for crime investigation?
- While investigating a murder case, the Delhi Police has asked the Delhi High Court to direct the UIDAI to match a suspect’s photograph and chance prints with the Aadhaar database to help it identify the accused.
- In a first-of-its-kind case, Delhi Police approached Delhi High Court in February under Section 33(1) of The Aadhaar Act, wherein a judge of a High Court can order the disclosure of information on identity in certain cases.
- In a murder case Delhi Police recovered fingerprints from the spot and footage from CCTV cameras in the crime area showing one of the suspects.
- However, the fingerprints and pictures did not match with any of the data already available with the police.
- Investigators now wants to cast the net wider, using Aadhaar’s biometric database that will help Police to identify the accused in this case.
- In response to a petition filed by Delhi Police in the High Court, UIDAI has said that it cannot share Aadhaar biometric data for crime investigations.
- The Aadhaar Act requires the UIDAI to ensure confidentiality and security of the identity information it collects.
- Section 29 of the Aadhar Act prohibits it from sharing core biometric information — fingerprint, iris scan or any such biological attribute — with any agency “for any reason whatsoever”.
- However, there is a national security exception — an officer not below the rank of the Secretary to the central government can order disclosure of information including identity information or authentication record in the interest of national security
- Reasons why UIDAI is opposing Delhi Police Plea
- Prohibited by Law: Section 33, the provision under which Delhi Police has approached the court, allows the disclosure of only identification information including photographs or authentication records, but no core biometric information.
- Consent is mandatory: The UIDAI has also said that no Aadhaar data can be shared by any individual or entity with anyone without the consent of the resident or holder of the Aadhaar.
- Not Standardised for Forensic Purpose: UIDAI has also said it does not collect biometric information — iris scans and fingerprints — based on technologies, standards or procedures suitable for forensic purposes.
- Not Technologically Feasible: UIDAI had told the court that no “1:N” sharing of data was possible, it had to be done on a 1:1 basis only. The Aadhaar technology only permits biometric authentications which are done on a 1:1 basis for which it is necessary to have the Aadhaar number of an individual.
Mains Practice Question – Aadhar that has revolutionised the governance delivery is not without problems. Elaborate.
Note: Write answers to this question in the comment section.
MIND MAP
- how does one keep one’s Aadhaar data safe?, Is identity theft via Aadhaar possible?, So, What are the benefits of Aadhar?, What are the key features of the Aadhar Act?, What are the structural Problems that UIDAI faces?, What is Aadhar?, What was the recent circular issued by UIDAI and why it was withdrawn?











