Science and Technology
Context:
- Quantum computers have the potential to wreak havoc on the data, systems, devices, and networks we rely on daily.
- With traditional encryption models at risk and increasing military applications of quantum technology, the deployment of “quantum-resistant” systems has become the need of the hour.
Quantum Computing:
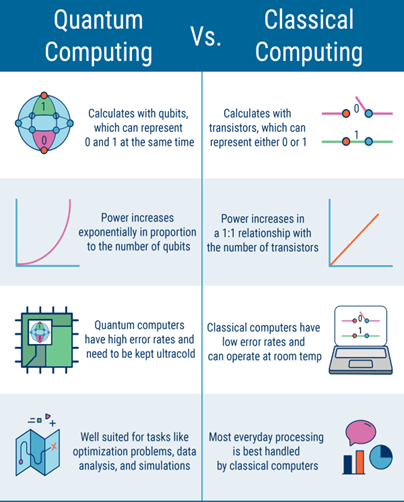
- Quantum computing aims to apply the principles of quantum physics — a body of science that seeks to describe the world at the level of atoms and subatomic particles — to computers.
- Whereas today’s computers use ones and zeroes to store information, a quantum computer relies on quantum bits, or qubits, which can consist of a combination of ones and zeroes simultaneously, something that’s known in the field as superposition.
- These qubits can also be linked together through a phenomenon called entanglement.
- Quantum computers are far more powerful than today’s machines and are able to solve complex calculations much faster.
- This could pose a problem for modern encryption standards.
What is Encryption:
- Encryption is the process of sending a scrambled message that only the intended recipient’s device can decode—allows private and public sectors alike to safeguard information.
- Quantum computers’ exponential leaps in processing power will render classical cyphers obsolete, potentially exposing troves of sensitive data across commercial entities, healthcare providers, government institutions, and billions of individual users.
- Experts are working to devise cryptographic schemes that can run on today’s computers, but that can also be used in ciphers to protect data against quantum attackers.
- RSA (Rivest–Shamir–Adleman) is a public-key cryptosystem that is widely used for secure data transmission.
- The day a quantum computer breaks an encryption for an attack is known as harvesting.
Concerns:
- Current protocols like the RSA will quickly become outdated. A quantum computer will be able to do break an RSA encryption – considered the gold standard for Public Key Encryption (PKE) in 10 seconds!
- This means that quantum cyberattacks can potentially breach any hardened target, opening a significant vulnerability for existing digital infrastructure. Hack proofing these systems will require considerable investments.
- Quantum computing can be exploited by military groups or criminal gangs, attacks on satellites, their systems, and base stations on Earth are seeing a steady uptick. Recent signal jamming of SpaceX Starlink satellites above conflict areas in the Ukraine forced him to announce a reallocation of resources toward cyber defense.
- In the hands of the enemy, a quantum computer capable of destroying RSA- encrypted data would have devastating effects on critical infrastructure and economy.
China specific concerns:
- China’s quantum advances expand the spectre of quantum cyberattacks against India’s digital infrastructure, which already faces a barrage of attacks from Chinese state-sponsored hackers.
- Cyber risks arising from quantum computing are accentuated by the lead taken by some nations in this sector. For example, the US National Quantum Initiative Act has already allocated $1.2 billion for research in defence-related quantum technology.
- Particularly worrying for India is the fact that China now hosts two of the world’s fastest quantum computers.
- India’s dependence on foreign, particularly Chinese hardware, is an additional vulnerability.
Indian Initiatives:
- Indian Army is developing cryptographic techniques to make its networks resistant to attacks by systems with quantum capabilities. The Army has collaborated with industry and academia to build secure communications and cryptography applications.
- This step builds on last year’s initiative to establish a quantum computing laboratory at the military engineering institute in Mhow, Madhya Pradesh.
- A joint team of the DRDO and IIT-Delhi successfully demonstrated a QKD link between two cities in UP — Prayagraj and Vindhyachal — located 100 kilometres apart.
- In 2019, the Centre declared quantum technology a “mission of national importance”. The Union Budget 2020-21 had proposed to spend Rs 8,000 crore on the newly launched National Mission on Quantum Technologies and Applications.
Suggestions:
- India must consider procuring the United States National Security Agency’s (NSA) Suite B Cryptography Quantum-Resistant Suite as its official encryption mechanism.
- The NSA is developing new algorithms for their cypher suite that are resistant to quantum cyberattacks. This can then facilitate India’s official transition to quantum-resistant algorithms.
- The Indian defence establishment can consider emulating the cryptographic standards set by the US’s National Institute of Standards and Technology (NIST) which has developed a series of encryption tools to handle quantum computer attacks. It has developed a series of four algorithms to frame a post-quantum cryptographic standard.
- After adopting these technical steps, India must start its national initiatives to develop quantum-resistant systems. For this, the government can fund and encourage existing open-source projects related to post-quantum cryptography along with active participation in the Open Quantum Safe project — a global initiative started in 2016 for prototyping and integrating quantum-resistant cryptographic algorithms.
- The country should start implementing and developing capabilities in quantum-resistant communications, specifically for critical strategic sectors.
- QKDs over long distances, especially connecting military outposts for sensitive communications, can be prioritised to ensure secure communications whilst protecting key intelligence from potential quantum cyberattacks.
- Eventually, this can help establish a nationwide communication network integrated with quantum cryptographic systems, thereby protecting cyberspace from any cross-border quantum cyber offensive.
- Finally, diplomatic partnerships with other “techno-democracies” — countries with top technology sectors, advanced economies, and a commitment to liberal democracy — can help India pool resources and mitigate emerging quantum cyber threats.
Way forward:
- As the Information Age gives way to the Quantum Age of computing it will require the largest global cryptographic transition in the history of computing. NATO, the U.S. government, the EU and other global institutions and governments around the world are preparing now for quantum attacks or Y2Q – the day a quantum computer breaks encryption.
- The world is moving towards an era in which the applications of quantum physics in strategic domains will soon become a reality, increasing cybersecurity risks. India needs a holistic approach to tackle these challenges. At the heart of this approach should be the focus on post-quantum cybersecurity.
Source: Indian Express
Previous Year Questions:
Q.1) Which one of the following-is the context in which the term “qubit” is mentioned ? (2022)
- Cloud Services
- Quantum Computing
- Visible Light Communication Technologies
- Wireless Communication Technologies











